Security
We understand your information and data is important. We will never ask for or store your passwords and you are always in control of access permissions.
In addition, we store very little information about you. We store minimal data about your tasks in our database and we encrypt everything we store so that anyone looking at the database would not be able to read the information.
What information do we keep about you? The email account you’ve authenticated with and the column names on your Board. We keep configuration settings on file per connection, but that does not include your username and password; instead we use a token. We sync your tasks using that token and store basic information about your tasks such as the name, ID , due date and status (anything you can see in OneTaskList). The permission to use this token can be revoked by you via the system we are reading them from. Again, we encrypt any of this information so that anyone looking at the database would not be able to read it.
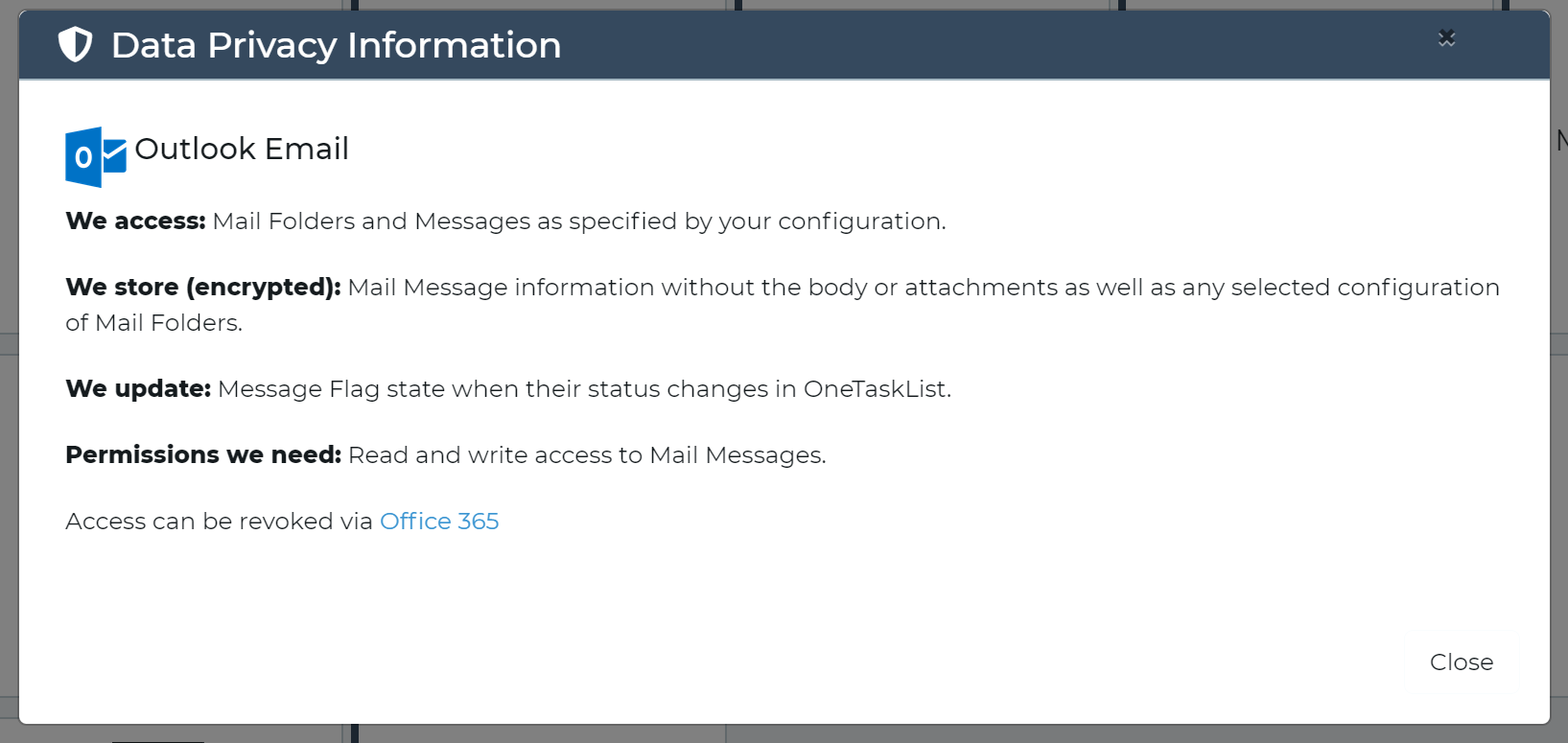
To see what information we access and store for each connection, please click on the “data privacy” button (the shield icon) for the connection.

We do perform some analysis on your task management behaviours, but now, this is limited to such insights such as “which source system did they come from? (e.g. Gmail, Outlook, Jira, etc.)” and “How much time elapses before they are marked as ‘done’ in our system”. In time, we hope to provide you tips to improve your ability to manage your tasks. If you’ve got questions about security or any concerns, you can always get in touch with us at info@onetasklist.com or look at our
Security FAQs
Q: What information do you store about me?
A: As per our Privacy Policy we store (encrypted) your first name, last name, email address, auth provider ID and (where available) your public profile image URL.
Q: What information do you store about my tasks?
A: Minimal information including task name, ID, Due Date, status and selected meta data so we can identify your tasks and show information on your board. To avoid storing excess, potentially sensitive data in our systems we provide links back to your tasks.
Q: Is there a way for you to look at the details of my tasks?
A: All your task details are encrypted in our database so authorised or unauthorised access to your task information is prevented. Any attempt by us to develop any software to access this information would be in violation of our privacy policy and leave us open to litigation.
Q: How do you display the details of my tasks in OneTaskList?
A: We display the name of the task (and any additional meta data tags) on the card on your board. This is loaded encrypted from the database, decrypted on the server and transmitted securely via HTTPS to ensure it is encrypted in flight.
Q: Is this safe to use for my company task systems?
A: Yes, the nature of our product means that trust and security are critical to its success. We have adopted best practices across all levels of the application architecture to ensure
Q: How do I delete my login and information if I want to?
A: A request to delete your account and any associated data can be made by the feedback form on the application or via email to us directly at info@onetasklist.com. By law we are required to comply with this request within 30 days.
Q: What happens if I don’t have access to a system anymore (e.g. I change jobs, or I forget my username/password for a system)?
A: If you lose access to authenticate via the account you signed up with, you will need to contact the original authentication provider (e.g. Google, Microsoft, Facebook, etc.) and resolve your access directly with them. If you lose access to a specific connection (for example, your access is revoked by the source system), then the connection will no longer be able to import new tasks or access the task information via linking to the task. It is then up to you if you want or need to delete the connection and related task headings via the application.
Q: What security protocols do you use to secure my data?
A: Communication between your browser and the server as well as internal communication between our servers is using HTTPS TLS 1.2. I. The data in the database is stored not only using Transparent Data Encryption, but additionally all your readable strings are encrypted using the algorithms AES-256-CBC for confidentiality and HMACSHA256 for authenticity.
Q: What security policies and procedures do you have in place?
A: We currently have the following policies in place and are frequently reviewing them. (links provided where currently public)
- Privacy Policy
- Terms and Conditions
- Information Security Policy
- Risk Management Policy
- Authorised Access Policy
- Data Retention Policy
Q: How are you storing and protecting my logins to my task systems?
A: We store the access tokens in our database which is hosted and managed in a service by Microsoft. These tokens are encrypted with your personal key which is in turn encrypted by additional keys held in a system our application can access but individuals at our company cannot.
Q: Has the system been verified by Google?
A: Not yet. We are currently planning this verification, however as it is an expensive process and we are still in the processing of validating the product through our beta release. Potential pivots in functionality would mean a potential repeat of any verification.
Q: Has the system been penetration tested?
A: Not yet. We see this as a critical step in validating our product. Again, as we are in beta and still validating the product functionality, this effort would need to be repeated when we make any major feature changes.
Q: Do you comply to security protocols (such as ISO27001 or SOC2)?
A: OneTaskList is hosted using Microsoft Azure PaaS services and hence we don’t manage any of the servers ourselves. They are ISO 27001 and SOC2 certified and are regularly audited by 3rd parties.
Q: Who at OneTaskList has access to my data?
A: The databases are only accessible by a select few administrators who are responsible for maintaining and monitoring the application. All these administrators operate under our Information Security and Authorised Access policies and are required to pass Australian Police background checks.